Condusiv Help Center
Help Center / Product FAQs & Troubleshooting / Undelete FAQs
Undelete FAQs
General Information
Undelete works differently and by replacing the Recycle Bin at the file server, we can intercept those files and present them for recovery.
Yes! Undelete protects files deleted from your Cloud Servers too! Organizations transitioning from on-premise systems to cloud infrastructure (i.e. Infrastructure as a Service – IaaS) can maintain consistent file protection and recovery capabilities by deploying Undelete on their cloud servers. This ensures continuity in data management practices and enhances overall operational efficiency within the organization.
If you have a current Undelete subscription, we offer the ability to transfer existing Undelete licenses from on-premise systems to cloud servers so customers can leverage their investments efficiently. This flexibility reduces the overhead associated with adopting new technologies and reinforces the value of Undelete. Please contact customer support or your account manager for assistance.
Overall, incorporating Undelete into cloud server environments offers comprehensive file protection and recovery benefits, safeguarding against data loss and supporting uninterrupted business operations.
2. Undelete captures files deleted within applications—the Recycle Bin does not.
3. Undelete captures files deleted from the Command Prompt—the Recycle Bin does not.
4. Undelete captures files deleted within the File Manager – the Recycle Bin does not.
5. Windows does not have a native undelete facility to recover files that have been fully deleted.
6. Undelete allows you to search for deleted files by names or partial names.
7. Undelete includes Emergency Undelete, which allows you to recover previously deleted files, even those deleted from the Recycle Bin.
8.The Undelete program identifies the ownership of the deleted file/folder as well as the person who deleted the file/folder.
Like Undelete Server Edition, the Professional Edition can recover files from the computer where it is installed, and it can also recover files from computers that have Undelete Server Edition installed.
The Undelete Client component, which is used with Undelete Server Edition, allows you (or more importantly, your users) to find and recover deleted files from remote Recovery Bins, such as those on a file server. The Undelete Client operates similarly to the Recovery Bin interface in Undelete Professional Edition, except it only “sees” Recovery Bins on remote systems. It does not have a “local” Recovery Bin where deleted files are stored. Users are only shown and allowed to recover files on shared network drives for which they have sufficient ownership or system privileges. NTFS permissions are applied and users will not be able to restore data from file shares they do not have permission to.
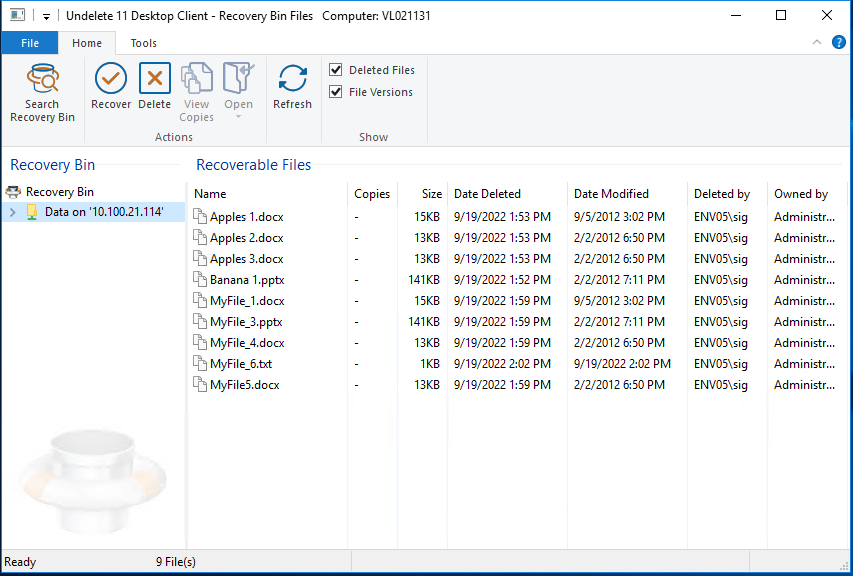
From the Undelete Server version, you can Push Install the Client to the system(s) OR you can take the Client Setup files from the following location:
C:\Program Files\Condusiv Technologies\Undelete\ClientPushInstallFiles
You can then copy the Undelete Client setup.exe file to the respective system and install it there. Note that the Client is used to connect to the Recovery Bin of the mapped drives of servers that are running Undelete.
The Undelete Client saves time and trouble for System Administrators and Help Desk personnel by enabling users to recover their own deleted files from remote file servers. Undelete Server includes unlimited Client licenses.
Restoring files with Undelete takes just seconds and is much faster restoring files from backups. Additionally, any work done since the last backup is not lost and doesn’t have to be recreated. Undelete is not a replacement for a good backup system. A back up system is the correct tool in the event of minor or major disasters, like a system crash. Undelete is the correct tool for individual file protection. You need both.
Installation & Licensing
Undelete 11 is an intelligent in-place upgrade package and will detect if Undelete 10 is installed and use all the current settings and keep all recoverable files. No uninstall of Undelete 10 is required. Also, a reboot is not needed or required.
Method 1:
Please take these steps to convert Undelete Trial version to a paid Subscription license:
- Double Click the Recovery Bin to launch Undelete.
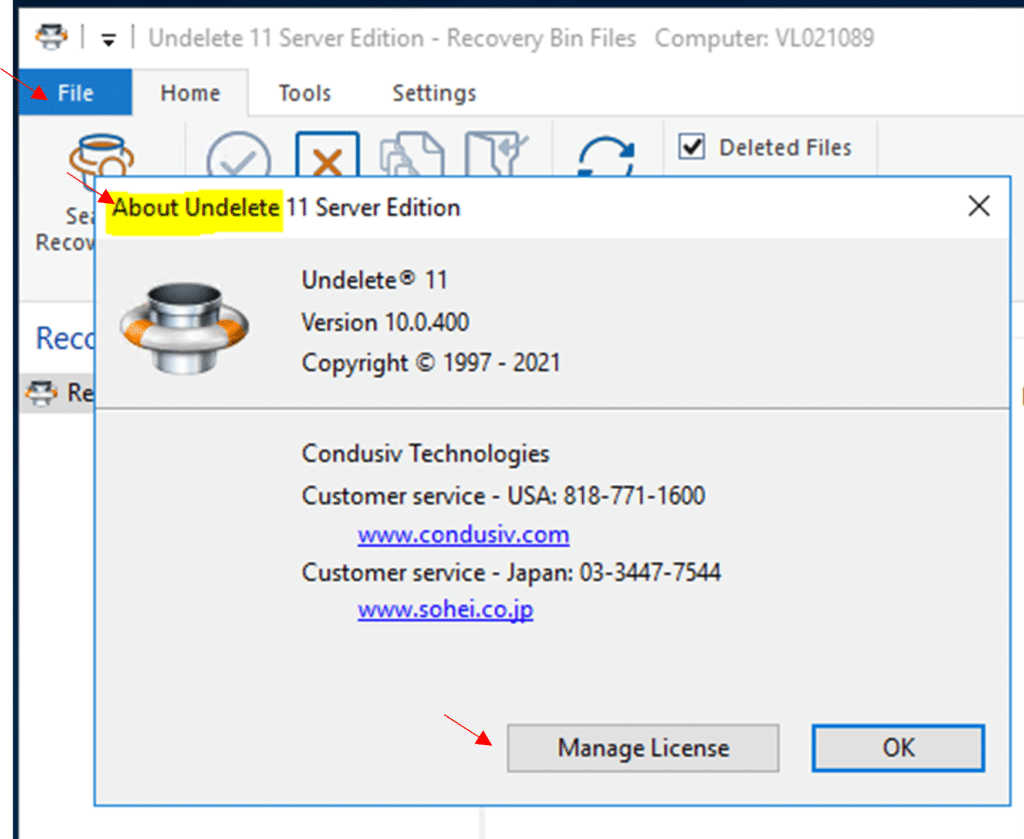
- Go to File → About
- Click on the Manage License button
- Enter your new key and click the Apply button
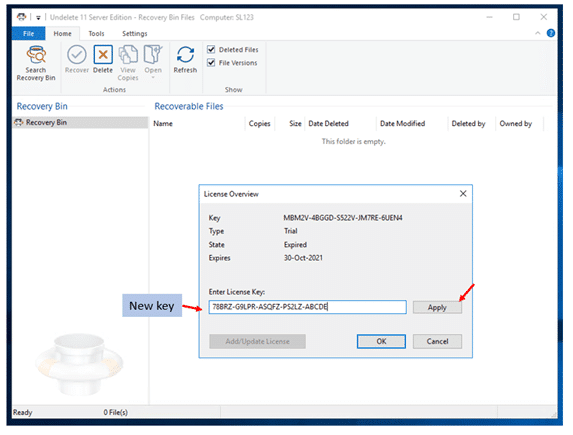
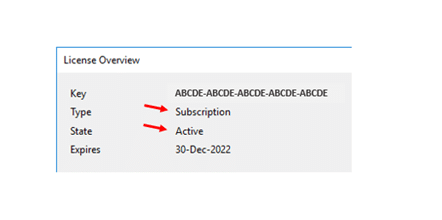
When the new key is successfully applied, the license data will update:
Method 2:
This is another way to convert an Undelete Trialware installation to a paid Subscription:
- Create a .key file (How to Create a .key file)
- Place the .key file in the Undelete install folder:
C:\Program Files\Condusiv Technologies\Undelete - Restart the Undelete Service or restart your system
The download package for Undelete will include one of these two packages:
![]()
To extract the setup.exe files for Undelete Server, Pro, and Client simply install FullEnglishUndeleteServer. The setup.exe files are extracted and placed in the installation folder for Undelete.
Undelete does not require a reboot on install or uninstall.
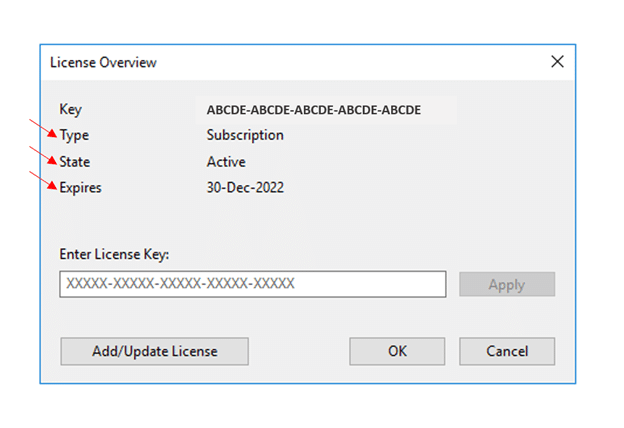
To enter your license key, double click the Recovery Bin icon on the Desktop or click the start button and type Undelete. This will launch Undelete and on initial startup, it will bring up the License Overview page where you can enter your license key.
Your license key is in “Subscriptions & LIC Keys” within My Account.
When your key has been successfully added, you will see the license Type, State, and Expiration fields are populated. Your system will need direct access to the internet in order to activate the license. You will not be able to recover documents from the Recovery Bin until the license has been activated.
Another way to access the License Overview page is from the File → About menu:
Undelete does not require a reboot after install or uninstall.
Undelete does support a few different methods of Administrative Push Install. Depending on the systems you use to push installations, you can push Undelete using either a Setup.exe package or an .MSI form of the Undelete installation package.
Undelete Server also includes (as part of its installation), a feature called Undelete PushInstall which can be found by selecting Start and Programs and then selecting Condusiv Technologies. This allows you to select specific computers in your domain to push the different flavors of the Undelete software to.
Should you need assistance getting the appropriate push install package (Setup.exe or .msi) please submit a Technical Support Request for assistance.
The directory view of the Undelete Push install is not Active directory compliant. If you need to push Undelete to another system that is on your network but not listed in the view. You would need to obtain the setup.exe for that product, copy it across to the target system and install it locally.
An alternative to typing in the license key to activate the product is to use a .key file which is just a text file with the file type name changed to ‘key’ and contains the license key.
Undelete, DymaxIO, and CMC will pick up a .key file placed in the same folder as the setup.exe file and automatically license the product during the installation process.
Take these steps to create a .key file.
Open Notepad and paste in the license key.
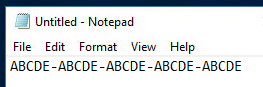
Click File → Save As.
Change the “Save as type:” field to “All Files (*.*)”
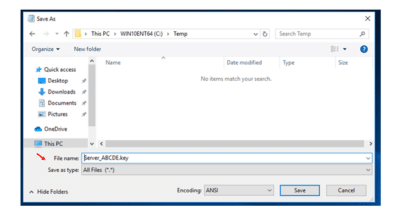
Name the file and give it a .key extension.
Place this file in the same folder as the setup.exe file and it will be picked up and automatically license the product.
Alternatively, if you need to install the key after installation, you can place the .key file in the product installation folder and restart the product service which will automatically license the product.
We advise that you right click on the Recycle Bin on your desktop to see if the check box for “Disable the Recycle Bin” has been checked. If you find it is, the default Windows Recycle Bin will not capture files that are deleted from the system. Clearing this check box will restore normal Recycle Bin functionality.
Recovery Bin Functionality
Yes it can! Undelete even includes a “Versioning” feature which can help to capture files that are overwritten or revised such as Microsoft Word and Excel files.
To exclude a complete disk volume, do these steps:
1. Within the Properties dialog box of the Recovery Bin menu, select Enable Recovery Bin individually on each drive.
2. Using the tabs, select the drive you wish to exclude from Recovery Bin processing.
3. Clear the Enable Recovery Bin on this drive check box.
This will exclude the entire drive. Note: You cannot use this solution if you have the One Recovery Bin location for all drives radio button selected.
The Recovery Bin Properties option allocates a default maximum size for the Recovery Bin to be 20% of the total available free space on the disk. You can adjust this maximum by selecting the appropriate disk volume tab within the Recovery Bin Properties dialog box. When a file deletion causes the Recovery Bin to fill to 100% of its maximum size, just enough files will be purged from the Recovery Bin to make room for the new file. Files are purged from the Recovery Bin on a first-in, first-out basis. The files that have been in the Recovery Bin for the longest time will be the first files purged from it.
Note that you can also purge files from the Recovery Bin based on how long the files have been in the Recovery Bin. You can specify how many days files should be left in the Recovery Bin before being purged. This “date-based” purge feature is available from the individual drive tabs and the Common Bin tab. As an option, date-based purging can be used together with the Auto Purge function. You can adjust the number of days for it to retain files. The box in the UI must be checked for this feature to be turned on. If not all captured deleted files will be retained indefinitely unless purged for another reason.
In cases such as this, it’s likely that files are compounding within the InProgress folder of that volume. The InProgress folder, found within the X:RecoveryBin folder of that volume (which by the way will be a hidden folder), is a folder intended for files to pass through while on their way to the Volumexxx-xxx-xxx folder that’s also found under X:RecoveryBin. The InProgress folder is not supposed to hang on to files for an extended period of time but where files being deleted don’t include System and Administrator rights with FULL CONTROL, files may end up in the InProgress folder without the ability to be moved out.
In cases such as this, a restart of the Undelete service can force such files to be imported properly but where this situation continues to repeat, it may be necessary to employ the CACLS command to set the volume and all files and folder on it, to include the System and Administrator rights, with FULL CONTROL.
To do this, open a Command Prompt and go to the root of that volume. From there, type the command:
CACLS */e /t /c /g Administrators:F System:F
That command should do nothing to the existing permissions on all of the files aside from ensuring those accounts are given full rights but as with any sweeping change such as this, it’s a good idea to have a full backup in advance.
If Undelete is not capturing some files, first check the Undelete Exclusion List to make sure they aren’t listed there. If they are not listed, then there is likely a permissions issue. Undelete requires file permissions to include either Everyone: Full Control, or both Administrators: Full Control and System: Full Control. If a file does not have these settings, Undelete is not allowed to access it. To prevent this, you should add Administrators: Full Control and System: Full Control to all files.
This is a process that appends to your NTFS Permissions without overwriting what has been set up.
SPECIAL NOTE: if you are not at the root of the partition in question you must set your default there:
CD /D drive_name:
Note the command line, which is case sensitive. The spaces between qualifiers are also required:
cacls * /e /t /c /g Administrators:F SYSTEM:F
SPECIAL NOTE: If you see this message: “Unable to perform a security operation on an object which has no associated security” you are executing this from a FAT partition, you must set default to the NTFS partition.
ANOTHER SPECIAL NOTE: If you see this message: “No mapping between account names and security IDs was done” you have misspelled the name of your domain or one of the other groups.
This command would EDIT (/e) the ACLs rather than REPLACE them and recursively apply them (/t) to subdirectories. CACLS will continue (/c) even when it hits an open file. Any number of ACCOUNT:PERM may follow the GRANT (/g) switch. There is additional flexibility built into the cacls command – its only limitation is the dearth of selections for PERM values.
The first time Wipe Free Space runs on a volume the process can take a long time (hours) but subsequent passes will go faster. The amount of free space on the volume and the size of the unused portion of the MFT are factors that influence the speed of the process. If manual Wipe Free Space is expected to be used on a volume in the future, we recommend enabling automatic Wipe Free Space on the volume and allowing it to run in the background—subsequent manual Wipe Free Space operations will then only need to wipe the more recently modified free areas of the disk.
When you open a folder in the Recovery Bin, Undelete is doing much more work than Windows Explorer. Undelete has to gather information on who deleted the file, the path of the file, and permissions data – this extra work takes up time.
An issue was found with the current Undelete 11 edition. When setting up a Common Recovery Bin, it allows you to select a Volume and a Path/Folder name for the Common bin to reside at. If no Path/Folder name is given, it uses the default “RecoveryBin” folder. The Auto purge will work fine with this default name. If any other Path/Folder name is selected, the Auto Purge feature does not work properly, and the Common Bin has to be manually purged. This will be addressed in a future release.
It is likely that Undelete can’t display the files captured within the Recovery Bin GUI when they are deleted because the NTFS security settings have been set in a way that does not allow the Undelete service to have access.
The problem comes from using Windows Explorer to modify security settings globally on disk volumes, directories, and files. This method of applying security settings is less than optimal. A more appropriate method is to execute the following command line from the root of the partition:
(Note: If you are not at the root of the partition in question you must set your default there: CD /D drive_name: )
Now the command line:
CACLS * /e /t /c /g Administrators:F System:F
(Note: If you see the message, ”Unable to perform a security operation on an object which has no associated security,” you are executing this from a FAT partition. You must set the default to an NTFS partition.)
This command will edit (/e) the ACLs, rather than replace them, and recursively apply them (/t) to subdirectories. CACLS will continue (/c) even when it hits an open file. Any number of ACCOUNT:PERM parameters may follow the grant (/g) switch. There is additional flexibility built into the CACLS command—its only limitation is the dearth of selections for PERM (permission levels) values.
You also may need to add System and Administrators to the drive itself. Do that through Windows Explorer with these steps:
1. Start Windows Explorer.
2. Right-click the partition in question.
3. Click Properties.
4. Click the Security tab.
5. Click the Permissions button.
6. If Administrator is not listed, click Add and select Administrator.
7. Highlight Administrator.
8. Set Type of Access to Full Control.
9. If System is not listed, click Add and select System.
10. Highlight System.
11. Set Type of Access to Full Control.
12. Clear the Replace Permissions on existing files check box (it is checked by default).
13. Click OK.
If you still have a problem, open the Undelete GUI and check the Properties dialog box. If the partition is displayed, click Apply to create the Recovery Bin directory.
Troubleshooting & Errors
Run the following steps to manually uninstall Undelete if the normal uninstall procedure fails:
1. From the Windows Desktop, click START, then RUN
2. Type REGEDT32 for the command and click OK
3. Double-click HKEY_LOCAL_MACHINE on local machine,
4.Double-click SOFTWARE
5. Double-click Microsoft
6. Double-click Windows
7. Double-click CurrentVersion
8. Double-click Uninstall
9. In the top of the listing below Uninstall, you will see a series of GUIDs, they look similar to this: {842BD6DD-0B8D-4C24-91F7-C553283A4971}, highlight each until you find one in which the DisplayName field in the right-hand pane says either UndeleteWorkstation or UndeleteServer (depending on what you have installed) in the ‘Data’ column.
10. After selecting the correct GUID, double-click the UninstallString field in the right hand pane.
11. This will bring up an Edit String window with the Value data highlighted. Copy that data.
12. From the Windows Desktop, click START, then RUN and paste the copied data from the UninstallString field.
13. Click OK and the uninstall process will begin. It should complete successfully.
If these steps fail, apply the manual uninstall steps below:
1. Delete the following Undelete registry keys:
HKEY_LOCAL_MACHINESOFTWAREExecutive SoftwareUndelete
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows CurrentVersionUninstallUndelete
*** ONLY version 1.x ***
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows CurrentVersionUninstall6E3B3178-11D3-89A2-0060975B6A87
*** OR the code that displays Undelete on the right pane in the ProductName field (version 2.0+)***
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesUdDrv
HKEY_LOCAL_MACHINESYSTEMCurrentControlSet ServicesUndeleteService
HKEY_CLASSES_ROOTCLSID{260546E1-E9B4-11d0-910F-0060975EC077}
HKEY_CLASSES_ROOTCLSID{912F3920-B440-11d0-90DB-0060975EC077}
HKEY_CLASSES_ROOTCLSID{94665C20-C645-11d0-90EE-0060975EC077}
HKEY_CLASSES_ROOTCLSID{C2BD5645-F09A-11d0-9969-0060975B6ADB}
HKEY_CLASSES_ROOTCLSID{E2B090D0-BAA3-11d0-90DE-0060975EC077}
HKEY_CLASSES_ROOTAppID{260546E1-E9B4-11d0-910F-0060975EC077}
HKEY_CLASSES_ROOTAppID{912F3920-B440-11d0-90DB-0060975EC077}
HKEY_CLASSES_ROOTAppID{94665C20-C645-11d0-90EE-0060975EC077}
HKEY_CLASSES_ROOTAppID{C2BD5645-F09A-11d0-9969-0060975B6ADB}
HKEY_CLASSES_ROOTAppID{E2B090D0-BAA3-11d0-90DE-0060975EC077}
HKEY_CLASSES_ROOTAppIDDeskUnd.exe
*** ONLY if Undelete Workstation is installed ***
HKEY_CLASSES_ROOTAppIDNetUnd.exe
*** ONLY if Undelete Server is installed ***
HKEY_CLASSES_ROOTAppIDUdBin.exe
HKEY_CLASSES_ROOTAppIDUdFat.exe
HKEY_CLASSES_ROOTAppIDUdNtfs.exe
HKEY_CLASSES_ROOTAppIDUdServe.exe
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionExplorerDesktop
NameSpace{27e983f0-5b88-11d1-a7d8-006008060078}
HKEY_CLASSES_ROOTCLSID{27e983f0-5b88-11d1-a7d8-006008060078}
2. Set the startup type of the “Executive Software Undelete” service to “Disabled”.
3. Reboot.
4. Delete the Undelete directory from beneath the Execsoft directory. All of the files (bar the driver) are in the installation directory. The driver exists in the following path: %systemroot%System32DriversUdDrv.sys.
5. If the “Recycle Bin” icon is not on the desktop, create the following key:
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionExplorerDesktop
NameSpace{645FF040-5081-101B-9F08-00AA002F954E}
6. Set the default value of the key to “Recycle Bin” (or the localized version of the tag).
7. Use the “Recycle Bin” properties dialog to configure it as desired.
Note that the “Executive Software Undelete” service will continue to be listed in the Services window until the next reboot.
First, ensure that you are running the very latest build of Undelete. You can check that by select Help and then About Undelete from Undelete’s main menu. In some cases Undelete is leaving the files in the InProgress folder when they are deleted, because the NTFS security settings have been set in a way that does not allow the Undelete service to have access.
The problem comes from using Windows Explorer to modify security settings globally on disk volumes, directories, and files. This method of applying security settings is less than optimal. A more appropriate method is to execute the following command line from the root of the partition:
(Note: If you are not at the root of the partition in question you must set your default there: CD /D drive_name: )
Now the command line:
CACLS * /e /t /c /g ”YOUR_DOMAINDomain Admins”:F
(Note: If you see the message, ”Unable to perform a security operation on an object which has no associated security,” you are executing this from a FAT partition. You must set the default to an NTFS partition.)
This command will edit (/e) the ACLs, rather than replace them, and recursively apply them (/t) to subdirectories. CACLS will continue (/c) even when it hits an open file. Any number of ACCOUNT:PERM parameters may follow the grant (/g) switch. There is additional flexibility built into the CACLS command—its only limitation is the dearth of selections for PERM (permission levels) values.
You also may need to add System and Administrators to the drive itself. Do that through Windows Explorer with these steps:
1. Start Windows Explorer.
2. Right-click the disk volume in question.
3. Click Properties.
4. Click the Security tab.
5. Click the Permissions button.
6. If Administrator is not listed, click Add and select Administrator.
7. Highlight Administrator.
8. Set Type of Access to Full Control.
9. If System is not listed, click Add and select System.
10. Highlight System.
11. Set Type of Access to Full Control.
12. Clear the Replace Permissions on existing files check box (it is selected by default).
13. Click OK.
If you still have a problem, open the Undelete GUI and check the Properties dialog box. If the disk volume is displayed, click Apply to create the Recovery Bin directory.
The Recovery Bin catches all files from the system, so it is very likely that these were file(s) that were deleted from the system or some other application and not by you. In this case, the security of that file can be set in such a way that administrators do not have the rights to delete them. They may be able to read them, but not delete them. The security user rights will need to be changed on the files before being deleted. Below is a current manual work-around for this.
1) Start up a Command Prompt window
2) Execute the following command which will grant Admin Users and System Users rights to delete any file in the RecoveryBin on the specified volume. Replace “x” with the drive letter of the volume where the files cannot be deleted.
CACLS x:RecoveryBin /E /T /C /G Administrators:F System:F
If this does not resolve the issue, you may find it necessary to run this command on each of your NTFS volumes.
SPECIAL NOTE: This command only needs to be executed on NTFS volumes.
ANOTHER SPECIAL NOTE: If you see this message: “No mapping between account names and security IDs was done” you have misspelled the name of your domain or one of the other groups.
This command would EDIT (/e) the ACLs rather than REPLACE them and recursively apply them (/t) to subdirectories. CACLS will continue (/c) even when it hits an open file. Any number of ACCOUNT:PERM may follow the GRANT (/g) switch. There is additional flexibility built into the cacls command – it’s only limitation is the dearth of selections for PERM values.
Error 1720 occurs when the Microsoft® Installer is unable to access the files needed to install the software. This situation can occur if the installation of the product was interrupted or had a failure.
This error can be easily fixed. Please see the instructions below:
http://www.articlesbase.com/operating-systems-articles/fix-windows-installer-error-1720-the-easy-way-1149825.html
This error occurs because there is a problem creating or writing to a folder. This could for one or several of these reasons:
A) You do not have the permissions required to install programs. To resolve this problem, you must be logged in as an administrator.
B) The folder is on a NTFS drive and permissions are set up for the folder that will prevent installation. Change that folder back to the default ‘EVERYONE’ permissions.
C) The hard drive is full. You have to free up hard drive space. For example, delete unnecessary files or uninstall programs that you do not use.
A file you are trying to update is in use. Make sure no programs are running while you are installing the software.
You need to adjust the permissions on the Installer folder to Full Control for the Everyone group. I also recommend that you set the permissions on the folder where you expanded the download to Everyone with Full Control.
The Installer may be a hidden directory that you may not see. If you can not see it, perform the following steps to make it visible.
1. Open My Computer
2. Select the Folder Options selection from the Tools menu
3. Select the View tab
4. Select the Show hidden files and folders radio button
5. Un-check the hide protected operating system files (Recommended) check box
6. Select Yes when the warning window comes up
7. Select the OK button
Then check for the Install or Installer directory in your %systemroot% (WinNT) directory. You should be able to see and setup the above recommended permissions.
Sometimes a reboot is necessary for the changes to take effect.
It should be noted that Undelete will only display folders within its GUI when it’s presenting deleted files from that drive, for recovery. If files have not been deleted against a particular volume then it will not display within the Undelete GUI.
If you’re certain that files have been deleted for that volume and it’s still not showing within Undelete, please revisit the Properties section of Undelete and ensure that that drive is set to have a Recovery Bin enabled. You may also want to check the exclusion list to see if that volume has somehow been fully excluded by mistake. Lastly, if those settings don’t correct the situation, it may be that the permissions on that volume lack System and Administrator accounts with FULL CONTROL.
Since it’s necessary for these permissions to be present on any drive that Undelete cares for, it would be advisable to use the CACLS command to define those permissions for the volume in question.
To use this command, open a Command Prompt and go to the root of that volume From there, you can type:
CACLS */e /t /c /g Administrators:F System:F
That command should do nothing to the existing permissions on all of the files aside from ensuring those accounts are given full rights but as with any sweeping change such as this, it’s a good idea to have a full backup in advance.
Files that have been completely deleted (no longer in the Recycle Bin) can be overwritten. It is not possible to restore a deleted file after it has been completely overwritten.
This can happen when the Undelete Service did not get started completely before you attempted to open the Recovery Bin. The start-up process for the Undelete Service can take a moment or two so it’s best to wait a few minutes after installing the software or starting the system before you open the Recovery Bin. If you do find yourself in the situation where the “Gathering Recovery Bin Information” process seems to go on and on – stopping the service and restarting it may solve this problem. You can also re-boot the system and wait a bit before opening the Recovery Bin.
The Recovery Bin catches all files from the system, so it is very likely that these were file(s) that were deleted from the system or some other application and not by you. In this case, the security on that file can be set in such a way that Administrators do not have the rights to delete them. They may be able to read them, but not delete them. The security user rights will need to be changed on the files before being deleted. Below is a current manual work-around for this.
1. Start up a Command Prompt window
2. Execute the following command which will grant Administrators and System Users rights to delete any file in the Recovery Bin on the specified volume. Replace “x” with the drive letter of the volume where the files cannot be deleted.
ICACLS * /T /C /grant Administrators:F SYSTEM:F
If this does not resolve the issue, you may find it necessary to run this command on each of your NTFS volumes.
SPECIAL NOTE: This command only needs to be executed on NTFS volumes.
ADDITIONAL NOTE: If you see this message: “No mapping between account names and security IDs was done” you have misspelled the name of your domain or one of the other groups.
This command would EDIT (/e) the ACLs rather than REPLACE them and recursively apply them (/t) to subdirectories. ICACLS will continue (/c) even when it hits an open file. Any number of ACCOUNT:PERM may follow the GRANT (/g) switch. There is additional flexibility built into the icacls command – its only limitation is the dearth of selections for PERM values.
If you’re certain that files have been deleted for that volume and it’s still not showing within Undelete, please revisit the Properties section of Undelete and ensure that that drive is set to have a Recovery Bin enabled. You may also want to check the exclusion list to see if that volume has somehow been fully excluded by mistake. Lastly, if those settings don’t correct the situation, it may be that the permissions on that volume lack System and Administrator accounts with FULL CONTROL.
Since it’s necessary for these permissions to be present on any drive that Undelete cares for, it would be advisable to use the CACLS command to define those permissions for the volume in question.
To use this command, open a Command Prompt and go to the root of that volume From there, you can type:
CACLS */e /t /c /g Administrators:F System:F
That command should do nothing to the existing permissions on all of the files aside from ensuring those accounts are given full rights but as with any sweeping change such as this, it’s a good idea to have a full backup in advance.
Compatibility & System Requirements
Yes, Undelete can protect and recover files deleted from a NAS drive if the volume from the NAS drive shows up as a local Windows volume on the system where Undelete is running.
To find out if Undelete will work on your NAS device, open up Windows Disk Management. If your NAS device shows there then Undelete will work on your NAS and if your NAS device does not show there then Undelete will not work on your NAS.
Undelete does not currently support ReFS. It only supports just NTFS.
Here are the steps to install Undelete correctly in a clustered environment. 1. Install Undelete on the primary node in the cluster.
2. When the system reboots, move the disk resources group back to the primary node.
3. Launch Undelete and go to the Recovery Bin Properties. The local disk volume as well as the shared disks should be seen.
4. Click OK. This creates the Recovery Bins on the shared clustered disks that weren’t there during the reboot of the node.
5. Install Undelete on the other node and reboot.
6. Move the disk resources back to the node where you just installed Undelete (non-primary node).
7. Again launch Undelete and go to the Recovery Bin Properties. The local disk volume as well as the shared disks should be visible to Undelete.
8. Click OK and close Undelete.
9. Move the disk resources back to the primary node in the cluster and you are done.
By doing this, both nodes now have the device intercept driver and file filter loaded. The Undelete service is running on both systems (as a Service), but since the shared clustered disks are known ONLY to one system at a time, only files deleted by that controlling system are captured or moved into the Recovery Bins. There is no need to set up or change this service.
Yes it does. Within the properties of Undelete, you can actually define (for each individual volume) whether to capture files deleted from a Macintosh share.
The Undelete service, UdServe.exe, listens on a fixed port for incoming Undelete interface connections. This is port 13621, but if this port is busy, it will use port 14482. The Undelete interface will use whatever port the system assigns it for its end of the connection. If UdServe.exe is allowed to use one of its fixed ports and to accept incoming connections on it, and if the interface is allowed to use whatever ports are assigned to it and to request connections, the Undelete service and interface will connect and the product will work. If your firewall software stops incoming connection requests to all “unknown” ports, then it would need to be told about the two ports that UdServe.exe listens on for Undelete to work.
The port numbers that Undelete uses are in the registry in the HKLMsoftwareExecutive SoftwareUndeleteFrBin key. The value names are Port0 and Port1. If you want to change the ports to other unused ports you can, but you must change them to the same values on all systems running Undelete that you want to interconnect. You must also make sure at least one of the ports is unused by other software on their systems, or the Undelete service will not start up.
Undelete Server can be installed and run on some server appliances running Windows remotely via Terminal Services or locally through the use of a directly connected monitor/keyboard/mouse if the hardware supports that. Undelete can then be administered the same way, or by connecting to it from Undelete Server running on another box.
Undelete will show mapped shares the same on a server appliance running Windows as on any other server.
If your sole interest is protecting files on your NAS, you will first want to determine if Undelete will work on your NAS device. To do so, open up Windows Disk Management. If your NAS device shows there then Undelete will work on your NAS and if your NAS device does not show there then Undelete will not work on your NAS.
Absolutely. Undelete does not replace Backups or Shadow Copies, it supplements them. In the event of a need to restore the entire volume due to issues like a hardware failure, a Backup or Shadow Copy ensures the ability to restore the complete volume from the latest backup or shadow copy. This is particularly crucial, especially when dealing with a malfunctioning system disk. On the other hand, Undelete is designed to effortlessly recover files that have been ‘accidentally’ deleted by a user or, with the Versioning feature, recover different versions of edited files. It captures any changes made since the last backup or shadow copy, providing a valuable solution for file-level recovery.
There are no size restrictions for Undelete. By default, 20% of the free space on a volume is used for the Recovery Bin. So, the size of the Recovery Bin is dynamic depending on the free space on the volume. This percentage is settable, so you can make it less or more. By default, when the Recovery Bin fills up, the oldest ‘deleted’ files will be purged to make room for the newest ‘deleted’ files.